Difference between revisions of "Login"
Schwietzer (talk | contribs) |
|||
| (84 intermediate revisions by 4 users not shown) | |||
| Line 1: | Line 1: | ||
== HPC Account == | |||
The first requirement for logging in to the HPC cluster is that your University login (in the form <tt>abcd1234</tt>) is activated for HPC. This is done by signing in to https://konto.uol.de/ and then selecting ''Zugang zu HPC''. In the next step, you can select the research group from the drop-down menue by their Unix-names in the form <tt>aggroupname</tt>. If you do not know the correct group, you can check the list of [[Unix groups|Unix-group names]]. If your group is not listed there, please send an e-mail to {{sc}} with a suggestion for a group name, the name and e-mail of the head of the group, and a link to the group's home page. | |||
Other groups (not starting with <tt>ag</tt>) are only available for special cases, e.g. the group <tt>student</tt> for temporary access in the context of a lecture (we can also provide course accounts, if needed, please e-mail to {{sc}}). | |||
After you have requested an HPC account as explained above, you should receive an e-mail (usually within 24h) that your account is activated. After that you can follow the steps below to login to the HPC cluster. | |||
== Login nodes == | == Login nodes == | ||
The cluster provides four login servers that allow | The cluster provides four login servers that allow you to connect to the cluster (e.g. for submitting and monitoring jobs or editing of files). The login servers can be reached using the hostnames | ||
carl.hpc.uni-oldenburg.de | carl.hpc.uni-oldenburg.de | ||
eddy.hpc.uni-oldenburg.de | eddy.hpc.uni-oldenburg.de | ||
| Line 10: | Line 18: | ||
== Intranet == | == Intranet == | ||
If you want to connect to the cluster from a windows computer, you can use your favorite ssh client (MobaXterm, PuTTY, OpenSSH, WinSCP) on Windows-Computers or the command line on Linux-computers. | If you want to connect to the cluster from a windows computer, you can use your favorite ssh client (MobaXterm, PuTTY, OpenSSH, WinSCP) on Windows- and Linux-Computers or the command line (primarily on Linux-computers). | ||
=== Connect to CARL/EDDY using MobaXterm === | === Connect to CARL/EDDY using MobaXterm === | ||
| Line 37: | Line 45: | ||
You can even drag&drop files on the cluster with this sidebar, which makes handling files very easy. | You can even drag&drop files on the cluster with this sidebar, which makes handling files very easy. | ||
==== Using the file explorer properly ==== | |||
You can configure MobaXterm to always display the current directory and its contents on the left sidebar. To ensure that this is always up to date with what you see on the ssh screen, you should make sure that the session is propperly configured. | |||
If you want to make use of that function and to make sure that both screens are always are in sync, you need to slightly modify the ssh server as shown above. You will need to define the exact login node that you want to login to, and you have the coice between <tt>hpcl001 - hpcl004</tt>. As an example, instead of using <tt>carl.hpc.uni-oldenburg.de</tt>, you type in <tt>hpcl002.hpc.uni-oldenburg.de</tt>. | |||
Now, you just have to tick the box ☑<tt>Follow terminal folder</tt> down below the file manager, and you can conveniently keep track of whats going on in the folders while browsing through your directories. | |||
=== Connect to CARL/EDDY using PuTTY === | === Connect to CARL/EDDY using PuTTY === | ||
| Line 77: | Line 88: | ||
ssh -X abcd1234@carl.hpc.uni-oldenburg.de | ssh -X abcd1234@carl.hpc.uni-oldenburg.de | ||
== | === Connect to CARL/EDDY using the Remote Desktop Protocol === | ||
If you need a graphical user interface (GUI) when using the cluster, and X-forwarding is not sufficient or does not perform as needed, then you can use the ''Remote Desktop Protocol'' ([https://en.wikipedia.org/wiki/Remote_Desktop_Protocol RDP]) to connect to the HPC cluster. Using RDP, you can open a Linux desktop on a special login node (<tt>hpcl005.hpc.uni-oldenburg.de</tt>) and use applications with a GUI as if you are sitting directly at the login node. To use RDP, you simply need a RDP client program, which is available for all common operating systems (see below for Windows and Linux). | |||
In addition to the better graphics performance compared to X11-forwarding, the remote desktop also keeps running when your connection to the cluster gets lost. Once you have reconnected, you can continue working where you left. You need to actively logout from the remote desktop to shutdown your session. | |||
Please be aware, that the login node <tt>hpcl005</tt> has limited resources and is less powerful than the standard login nodes. If your GUI applications requires compute power, it is recommended that you run an interactive session on one of the compute nodes (see below). | |||
==== Remote Desktop Connection from a Windows machine ==== | |||
Windows natively supports RDP and provides a client program for it. To start the client just search for 'remote desktop' within the start menus search function and select the corresponding program that pops up. Now, you type into the input mask the following server adress and press enter: | |||
hpcl005.hpc.uni-oldenburg.de | |||
After that, a certificate warning may appear which you can safely ignore (just confirm to continue). Next, a login screen should appear and you have to type in your your credentials. Just use the same login information that you would enter when accessing the cluster the usual way. Finally, a Red desktop environment will open and you can start a termial from the application menue in the top left. If you have ever worked with a virtual linux machine (e.g. VirtualBox, VMWare), this should be familiar to you. To logout, click the power button symbol in the top right and then your name. | |||
Once you have started a terminal, you can start working just like you would on a standard HPC session with the benefit of having a real desktop environment for applications with a GUI. As an example, we coud start <tt>gnuplot</tt>: <br/> | |||
If you have not done yet, open a terminal by clicking ''Applications'' at the upper left corner and clicking on ''terminal''. <br/> | |||
Now you change the environment, load the module and start the program: | |||
hpcl005$ module load hpc-env/6.4 | |||
hpcl005$ module load gnuplot | |||
hpcl005$ gnuplot | |||
gnuplot> plot sin(x) | |||
After a short while, the windows with the plot of the sine functions will appear. | |||
==== Desktop Access via Linux ==== | |||
Various RDP clients exist for Linux, and depending on your distribution, one is maybe already installed by default. Exemplarily, we use the client [https://remmina.org/ Remmina] which comes natively on a lot of distributions, like Ubuntu. If you cannot start remmina directly, you could [https://remmina.org/jekyll/how-to-install-remmina/# install] it or use a different tool that supports RDP. CentOS users have to use the built in Remote Desktop Viewer ''Vinagre'', for which the usage is quite self-explanatory. | |||
The following instructions will show you how to start a RDP session with Remmina, but should be applicable to other clients as well:<br> | |||
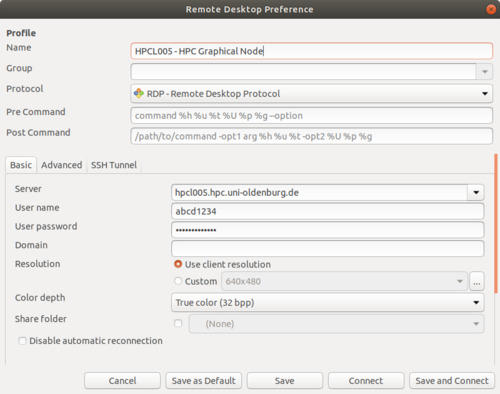
Start the tool by opening a terminal and typing in <tt>remina</tt> or. Now you fill in the form as follows: | |||
[[Image:remmina_hpcl005.png|500px]] | |||
* Name: The name for the connection is for you to decide. | |||
* Server: This is the login nodes server name. | |||
* User name: The username that you use for every other university service as well. | |||
* User password: The same goes for the password. | |||
* Color Depth: If you get an error message when leavin this on standard, try ''True colour (32 bpp)'' | |||
When you finished filling out the mask, click 'Save as Default' and then 'Save and Connect'. | |||
Now you will directed to the node. You may have to enter your credentials again, but after that you are good to go! | |||
==== Desktop Access via Mac ==== | |||
For Mac, there is a simple solution to get a visual access to our X11 login note: [https://apps.apple.com/de/app/microsoft-remote-desktop-10/id1295203466?mt=12 Microsoft Remote Desktop 10]. <br/> | |||
''(The HPC support team didn't test it though!)'' <br/> | |||
Although this is a program for accessing Windows machines, it can be used to get access to linux machines as well. <br/> | |||
Just download and install it from the app store, start the program and type in the host name (''hpcl005.hpc.uni-oldenburg.de''), your login name and the password. <br/> | |||
For more information you can visit the programs [https://docs.microsoft.com/en-us/windows-server/remote/remote-desktop-services/clients/remote-desktop-mac support website] | |||
==== Important: Best Practices ==== | |||
If you are using an RDP connection to <tt>hpcl005</tt>, please be kind to other and aware of the following | |||
* Save System Resources! | |||
** <tt>hpcl005</tt> is a login node with very few ressources. So please do not carry out heavy computations on this node! Instead run them remotely on a compute node using an [[Interactive Jobs|interactive SLURM job]] (in particular, take note of the command <tt>srun.x11</tt> that allows you to run graphical applications on a compute node). The login node <tt>hpcl005</tt> is only intended for users who are dependent on a graphical interface and is designed for short testing sequences. | |||
* Log out! | |||
** When you have finished your work on <tt>hpcl005</tt>, please quit your programs within the terminal and finally log out of the graphic node. You can do this by clicking the 'power button' on the upper right corner and selecting your name which is displayed on the menu. Now you should see a ''Log Out'' option. | |||
== Using SSH Keys for login == | |||
SSH keys can make the login with SSH a bit more comfortable because they can remove the need to enter your password. The general idea is that a pair of SSH keys, one public and one private, can be used for authentification. The keys can be protected by a password (and the general recommendation is to do so), but it is also important to note that '''the private key should never be given to anyone'''. This means among other things that the private key file generated in the process described below: | |||
# should not be copied, e-mailed or transferred otherwise to anyone else | |||
# should be kept only on your own computer(s) and not be copied to multi-user systems (e.g. like HPC centers) | |||
Please read the security considerations below for more details. | |||
The following instructions show you how to create and use SSH key with the HPC cluster: | |||
=== Creating SSH Keys === | |||
==== Windows ==== | |||
Microsoft started to roll out [https://www.howtogeek.com/336775/how-to-enable-and-use-windows-10s-built-in-ssh-commands/ its own ssh client]. But since it is not available on every Windows installation (and/or has to be activated), we use the SSH standard tool [https://www.putty.org/ PuTTY] (if you want to use the built-in SSH, you can use the Linux instructions below). | |||
First of all, you need to download PuTTY. Click [https://www.chiark.greenend.org.uk/~sgtatham/putty/latest.html here] and download the newest .msi file fitting your system (if you are not using an ancient PC, and are using Microsoft Windows, you very likely have to choose the <tt>64-bit x86</tt> installer ). Then, you execute the .msi file and click through the installation. You will need administrator privileges at this point. | |||
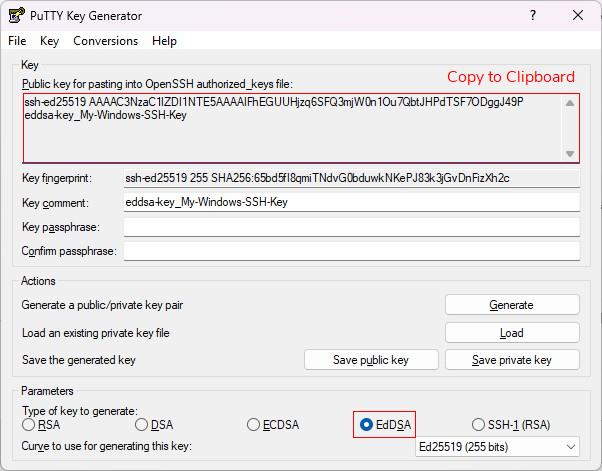
Afterward, start the program ''PuTTYgen'' by searching for it on the windows search bar. In ''PuTTYgen'' you can set the parameters for the generation of an SSH key, and it is advised to use a 255 bit long EdDSA key (''Ed25519''). Chosing the PuTTYgen default algorithm RSA can get you in trouble with more current servers as this algorithm is by now considered to be less safe. Next, click ''Generate'' and you will be asked to move around the mouse a bit to generate some randomness. This produces two keys: | |||
* Private key: This key is only for you and your devices. '''You must not hand this out to anybody!''' | |||
* Public key: This key can be transferred to any machine that you want to login to with SSH (see below). | |||
[[Image:PuTTYgen_Ed25519.jpg|PuTTYgen]] | |||
Optionally, you can now modify the key comment (it is recommended to add a meaningful comment) and also type in a passphrase (password) into the corresponding box. The password will be requested every time you establish an SSH connection using your key. '''Note:''' In general, you should type in a strong passphrase for your SSH key. Then, save the two keys on your local machine via the save buttons. The default location for SSH keys is: | |||
C:\Users\USERNAME\.ssh | |||
The files should be named <tt>id_ed25519.pub</tt> and <tt>id_ed25519</tt> (if you created EdDSA keys) for the public and private key, respectively. Before closing PuTTYgen, also copy the public key text in the upper box to the clipboard, for this first right-click->select all and then right-click->copy. | |||
==== Linux / macOS ==== | |||
Fortunately, Linux and macOS have all the tools you need already included. To generate a key pair, just open a terminal and type in | |||
$ ssh-keygen -t ed25519 -b 255 | |||
Generating public/private ed25519 key pair. | |||
Enter file in which to save the key (/home/username/.ssh/id_ed25519): | |||
Enter passphrase (empty for no passphrase): | |||
Enter same passphrase again: | |||
and follow the resulting prompts as shown above. You have the possibility to change the file name (typing enter uses the shown default) for the keys or to password protect it. '''Note:''' In general, you should type in a strong passphrase for your SSH key. After you have typed enter three times (one for the file, two for the passphrase), you have created two SSH keys: | |||
* Private key: This key is only for you and your devices. '''You must not hand this out to anybody!''' | |||
* Public key: This key can be transferred to any machine that you want to login to with SSH (see below). | |||
The keys can be found at this location <tt>$HOME/.ssh</tt> and the files are named <tt>id_ed25519.pub</tt> and <tt>id_ed25519</tt> (if you created EdDSA keys) for the public and private key, respectively. Now, copy the content of the public key into the clipboard by opening the following file with your favorite text editor: ''~/.ssh/id_ed25519.pub'' | |||
=== Add Public Key on HPC Cluster (or other Linux Hosts) === | |||
To enable the authentication with the generated key pair, you need to add the public key (<tt>id_ed25519.pub</tt>) to the authorized hosts list of the target system, e.g. the HPC cluster. This can be done in different ways: | |||
'''Using the clip-board''' | |||
After logging in to the cluster (not yet using the key), change to the hidden SSH folder in your <tt>$HOME</tt> directory: | |||
cd $HOME/.ssh | |||
and open the file ''authorized_keys'' with your preferred text editor. Go to the last line and paste the public key information that you copied clipboard in the step before. Make sure each key is in a separate line and do not overwrite existing keys in the file. Save the updated file and you are done. | |||
'''Using the public key file''' | |||
Alternatively, you can also copy the public key file <tt>id_ed25519.pub</tt> to the cluster. On Windows, use MobaXterm or WinSCP for that (do not overwrite any existing keys), on Linux you can use the command | |||
scp $HOME/.ssh/id_ed25519.pub abcd1234@carl.hpc.uni-oldenburg.de:.ssh/id_ed25519.pub.yourcomputername | |||
to achieve this. | |||
The next step depends on the format of your public key. If you used ''PuTTy'' to generate the key it will likely be in a format as seen by the output (truncated) from this command | |||
abcd1234@carl$ cat id_ed25519.pub.yourcomputername | |||
---- BEGIN SSH2 PUBLIC KEY ---- | |||
Comment: "eddsa-key-20230308" | |||
AAAAC3NzaC1l.... | |||
where the first line is a delimiter. Otherwise, you will probably see | |||
abcd1234@carl$ cat id_ed25519.pub.yourcomputername | |||
ssh-ed25519 AAAAC3NzaC1l.... | |||
where the key is in a single line. | |||
If you have the first format, you can add the key using | |||
$ cd $HOME/.ssh | |||
$ ssh-keygen -i -f id_ed25519.pub.yourcomputername >> authorized_keys | |||
or, if you have the second format, simply use this command | |||
$ cd $HOME/.ssh | |||
$ cat id_ed25519.pub.yourcomputername >> authorized_keys | |||
Please note the double <tt>></tt> for appending to the file <tt>authorized_keys</tt>. The commands also assume that you copied the public key to <tt>$HOME/.ssh/id_ed25519.pub.yourcomputername</tt>. | |||
=== Login Using SSH Keys === | |||
Once you have created the SSH keys and added the public key to the <tt>authorized_hosts</tt> file on the cluster, you are ready to use the keys for logging in to the cluster. | |||
'''Windows''' | |||
Here, you can choose between the SSH clients as explained above: MobaXterm and PuTTY. We will shortly discuss how to setup the usage of SSH key in both of them: | |||
# ''MobaXterm'': Assuming, that you already configured a session (if not, see above), right-click on the corresponding session profile and select ''Edit session''. At the rider ''Advanced SSH settings'', tick the box ''Use private key'' and browse to the private SSH key that you saved earlier on. You can start the session now to test if the login with the key is working. | |||
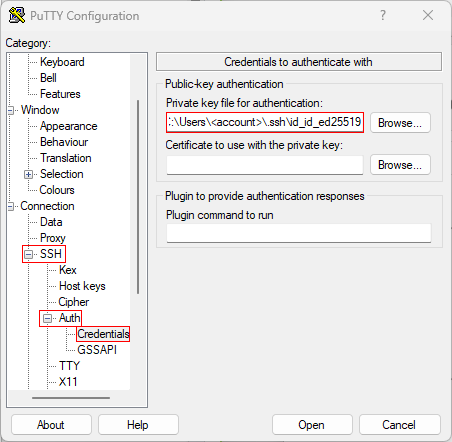
# ''PuTTY'': Start PuTTY and load one of the saved sessions if you already stored a configuration (just loading, not starting). If not, type in at ''Host Name'': ''abcd1234@carl.hpc.uni-oldenburg'' (change abcd1234 to your user name). | |||
:: In the left column, change to ''SSH -> Auth'' and insert your private key (''Private key file for authentication''). Change back to ''Session'' in the left column and save this session as a new file or overwrite an existing one. Start the session to test if the login with the key works. | |||
[[Image:PuTTY_config_marked.png|PuTTY]] | |||
'''Linux''' | |||
In Linux, you just use <tt>ssh</tt> as always | |||
ssh -X abcd1234@carl.hpc.uni-oldenburg.de | |||
If for some reason, this does not use the key (e.g. because the key has non-standard name), you can try | |||
ssh -X -i $HOME/.ssh/id_ed25519 abcd1234@carl.hpc.uni-oldenburg.de | |||
to tell ssh which private key to use. | |||
=== Using the SSH Agent === | |||
If you have created an SSH key with a passphrase (as is recommended) you need to enter the passphrase when you login: | |||
<pre> | |||
[local]$ ssh abcd1234@carl.hpc.uni-oldenburg.de | |||
Enter passphrase for key '/home/abcd1234/.ssh/id_ed25519': | |||
Last login: Thu Jun 4 10:34:46 2020 from 10.0.40.110 | |||
[carl]$ | |||
</pre> | |||
The difference between the passphrase for the key and the normal password is that the password is sent to the remote server while the passphrase is entered only locally. The local passphrase is therefore considered to be more secure. | |||
If you need to login multiple times to the remote server you can use the SSH agent to temporarily store the (unencrypted) private key. The command to start the agent and store a key are: | |||
<pre> | |||
[local]$ eval $(ssh-agent -s) | |||
Agent pid 97 | |||
[local]$ ssh-add $HOME/.ssh/id_ed25519 | |||
Enter passphrase for /home/abcd1234/.ssh/id_ed25519: | |||
Identity added: /home/abcd1234/.ssh/id_ed25519 (/home/abcd1234/.ssh/id_ed25519) | |||
</pre> | |||
Now you can login to the remote server | |||
<pre> | |||
[local]$ ssh carl.hpc.uni-oldenburg.de | |||
Last login: Thu Jun 4 17:42:15 2020 from 10.0.40.110 | |||
[carl]$ | |||
</pre> | |||
without entering the passphrase again. To remove the key you can use | |||
[local]$ ssh-add -d | |||
or kill the agent process using the <tt>pid</tt> printed above. | |||
You can also use | |||
$ ssh -A ... | |||
to enable agent-forwarding which allows you to use the private key also on the remote server, e.g. to login to a third system. Agent-forwarding removes the need to copy private keys to remote servers but it should only be used if it is really needed. | |||
=== Security Consideration === | |||
The SSH protocol has designed to allow a secure access to remote servers. However, there is never absolute security and even HPC centers can be the target of hackers. To minimize the risk, | |||
* do not give passwords or private keys to anyone (HPC support will never ask for your password) | |||
* consider using SSH keys as this reduces the risk for man-in-the-middle attacks | |||
* when using SSH keys kept your private keys secure and use a strong passphrase | |||
* do not copy private keys to multi-user systems such as HPC clusters | |||
* keep track of your authorized keys and use a pair of keys only for one system | |||
* if you think any of your accounts were compromised make sure to change passwords and SSH keys | |||
* if in doubt or if you detect unusual activities on your account contact {{sc}} | |||
== VPN: Internet / From Home== | |||
If you want to work from home or from any other place outside of the campus network, you have to establish a VPN tunnel to the university's intranet. After that, you can login to CARL or EDDY via ssh as described above. See the following instructions on how to setup the VPN tunnel (please note, that IT services have recently changed to the new provider/protocol GlobalProtect for VPN. The old Cisco VPN will be available for some time but eventually removed, of course not before an announcement): | |||
=== Windows === | === Windows === | ||
Download the | Download the VPN-Client from [https://v.uol.de/ this web site] and install it following the [https://uol.de/itdienste/services/netzzugang/vpn-client-fuer-windows/ instructions] of the IT Services. | ||
After installing the software, you only will be prompted for your university user name and password once. | |||
=== Linux === | === Linux === | ||
'''Download and Installation ''' | |||
At first, you will need the installation file from [https://software.uni-oldenburg.de/software/GlobalProtect/ here]. | |||
*For Debian and derivates (e.g. Ubuntu) you will need the ''.deb'' file. | |||
*For Red Hat, Centos, Fedora, Mandriva, OpenSUSE etc. you will need the ''.rpm'' file. | |||
* If you want/need, you can get the source files with the .tgz file should you need to compile the software by yourself. | |||
Now, you need to install the downloaded packet: | |||
For Red Hat, Centos, Fedora, Mandriva, OpenSUSE etc.: | |||
sudo rpm –ivh /path/to/GlobalProtect_rpm_x86_...rpm | |||
For Debian and derivates (e.g. Ubuntu): | |||
sudo dpkg –i /path/to/GlobalProtect_deb_x86_...deb | |||
Alternatively, you can change to the same directory as the downloaded file and make sure that you type in the missing version. e.g.: | |||
cd ~/Downloads | |||
sudo rpm –ivh ./GlobalProtect_rpm_x86_64-5.0.1.0-10.rpm | |||
After the installation, the executable <tt>globalprotect</tt> is callable from the command line. | |||
'''Configuration''' | |||
With ''globalprotect'' connect to the portal ''v-uol.uol.de'' <br\> | |||
Type in your credentials when asked. | |||
$ globalprotect connect --portal v.uol.de | |||
username: <Nutzerkontoname> | |||
password: <Nutzerkontopasswort> | |||
''Connecting...'' | |||
''Connected'' | |||
'''Status and Connection Details''' | |||
You can always check whether your connection is set up or not: | |||
$ globalprotect show --status | |||
Should you want to know more details about the current connection, you can type in: | |||
$ globalprotect show --details | |||
Finally, if you need to disconnect your VPN connection, you can use | |||
$ globalprotect disconnect | |||
'''Special Case: Linux Mint''' | |||
sudo | If you are using Linux Mint 19, you will additionally need to patch Global Protect after the installation. <br\> | ||
This is what you have to do: | |||
$ wget https://uol.de/fu/itdienste/download/update_gp_client.sh | |||
$ sudo sh update_gp_client.sh | |||
'''Fall back method''' | |||
If, after trying the above, you cannot setup you VPN using the ''Global Protect'', you can try to install ''openconnect'' with | |||
sudo apt-get install network-manager-openconnect-gnome | |||
After that, you can set up a connection with the terminal command: | |||
sudo openconnect --protocol=gp v.uol.de | |||
As long as the terminal stays open, every packet will be sent through the universitys network first. | |||
To terminate the connection, just close the Terminal or type in ''STRG + c'' | |||
Latest revision as of 10:07, 8 March 2023
HPC Account
The first requirement for logging in to the HPC cluster is that your University login (in the form abcd1234) is activated for HPC. This is done by signing in to https://konto.uol.de/ and then selecting Zugang zu HPC. In the next step, you can select the research group from the drop-down menue by their Unix-names in the form aggroupname. If you do not know the correct group, you can check the list of Unix-group names. If your group is not listed there, please send an e-mail to Scientific Computing with a suggestion for a group name, the name and e-mail of the head of the group, and a link to the group's home page.
Other groups (not starting with ag) are only available for special cases, e.g. the group student for temporary access in the context of a lecture (we can also provide course accounts, if needed, please e-mail to Scientific Computing).
After you have requested an HPC account as explained above, you should receive an e-mail (usually within 24h) that your account is activated. After that you can follow the steps below to login to the HPC cluster.
Login nodes
The cluster provides four login servers that allow you to connect to the cluster (e.g. for submitting and monitoring jobs or editing of files). The login servers can be reached using the hostnames
carl.hpc.uni-oldenburg.de eddy.hpc.uni-oldenburg.de
Using either of the two hostnames will connect you to one of the login servers which have the hostnames
hpcl00[1-4].hpc.uni-oldenburg.de
and are assigned in an round-robin fashion (to distribute the load on the login servers). You can also use these hostname to login to a specific server but should only be used when needed.
Intranet
If you want to connect to the cluster from a windows computer, you can use your favorite ssh client (MobaXterm, PuTTY, OpenSSH, WinSCP) on Windows- and Linux-Computers or the command line (primarily on Linux-computers).
Connect to CARL/EDDY using MobaXterm
"MobaXterm" is the recommend way to connect to the cluster from a Windows computer. The following lines will describe the basic usage of the program.
The newest version of MobaXterm can always be found here: Download
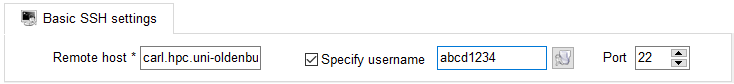
After downloading and installing you are ready to use the program. Once you opened it, click on "Session" in the top left corner. Fill in the following informations:
If you want to connect to EDDY, simply replace "carl" with "eddy" (-> eddy.hpc.uni.oldenburg.de).
As always, replace "abcd1234" with your own username. There are many settings that can be modified, for this example we will not change them though. Confirm by clicking on "OK". A new tab will open and you will be prompted to enter your password.
After typing it in and confirming it with ENTER you are succesfully connected to the cluster.
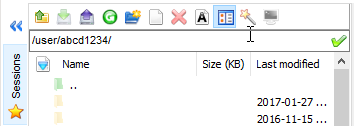
You will probably immediatly see a big difference to other ssh clients: you can easily browse through the folders on the clusters without using the command line. The sidebar will look like this:
You can even drag&drop files on the cluster with this sidebar, which makes handling files very easy.
Using the file explorer properly
You can configure MobaXterm to always display the current directory and its contents on the left sidebar. To ensure that this is always up to date with what you see on the ssh screen, you should make sure that the session is propperly configured. If you want to make use of that function and to make sure that both screens are always are in sync, you need to slightly modify the ssh server as shown above. You will need to define the exact login node that you want to login to, and you have the coice between hpcl001 - hpcl004. As an example, instead of using carl.hpc.uni-oldenburg.de, you type in hpcl002.hpc.uni-oldenburg.de. Now, you just have to tick the box ☑Follow terminal folder down below the file manager, and you can conveniently keep track of whats going on in the folders while browsing through your directories.
Connect to CARL/EDDY using PuTTY
We recommend to use "mobaXterm" since it offers more features and is more user-friendly. Nonetheless its your choise and if you want to use PuTTY you can follow these instructions:
Download the latest version of PuTTY from this link: Download
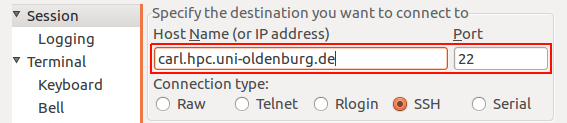
Enter the url "carl.hpc.uni-oldenburg.de" under the field "Host Name (or IP adress)":
Make sure the Port is set to "22" and the connection type is "SSH". Confirm by pressing the button "Open".
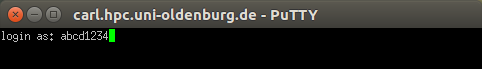
A new windows will popup and you have to type in your username (e.g. "abcd1234):
After you confirmed by pressing ENTER, you will be asked for your password. Type it in and confirm with ENTER again. You are now connected to the cluster.
If you want to connect to EDDY, simply replace "carl" with "eddy" (-> eddy.hpc.uni.oldenburg.de).
If you want to copy files from or on the cluster, you will have to use the program "WinSCP".
Connect to CARL/EDDY using the command line
Users of CARL can connect by typing:
ssh abcd1234@carl.hpc.uni-oldenburg.de
Similarly, users of EDDY login by typing:
ssh abcd1234@eddy.hpc.uni-oldenburg.de
If you want to use graphical applications on the login nodes (e.g. an editor like gedit) you need to enable X-forwarding:
ssh -X abcd1234@carl.hpc.uni-oldenburg.de
Connect to CARL/EDDY using the Remote Desktop Protocol
If you need a graphical user interface (GUI) when using the cluster, and X-forwarding is not sufficient or does not perform as needed, then you can use the Remote Desktop Protocol (RDP) to connect to the HPC cluster. Using RDP, you can open a Linux desktop on a special login node (hpcl005.hpc.uni-oldenburg.de) and use applications with a GUI as if you are sitting directly at the login node. To use RDP, you simply need a RDP client program, which is available for all common operating systems (see below for Windows and Linux).
In addition to the better graphics performance compared to X11-forwarding, the remote desktop also keeps running when your connection to the cluster gets lost. Once you have reconnected, you can continue working where you left. You need to actively logout from the remote desktop to shutdown your session.
Please be aware, that the login node hpcl005 has limited resources and is less powerful than the standard login nodes. If your GUI applications requires compute power, it is recommended that you run an interactive session on one of the compute nodes (see below).
Remote Desktop Connection from a Windows machine
Windows natively supports RDP and provides a client program for it. To start the client just search for 'remote desktop' within the start menus search function and select the corresponding program that pops up. Now, you type into the input mask the following server adress and press enter:
hpcl005.hpc.uni-oldenburg.de
After that, a certificate warning may appear which you can safely ignore (just confirm to continue). Next, a login screen should appear and you have to type in your your credentials. Just use the same login information that you would enter when accessing the cluster the usual way. Finally, a Red desktop environment will open and you can start a termial from the application menue in the top left. If you have ever worked with a virtual linux machine (e.g. VirtualBox, VMWare), this should be familiar to you. To logout, click the power button symbol in the top right and then your name.
Once you have started a terminal, you can start working just like you would on a standard HPC session with the benefit of having a real desktop environment for applications with a GUI. As an example, we coud start gnuplot:
If you have not done yet, open a terminal by clicking Applications at the upper left corner and clicking on terminal.
Now you change the environment, load the module and start the program:
hpcl005$ module load hpc-env/6.4 hpcl005$ module load gnuplot hpcl005$ gnuplot gnuplot> plot sin(x)
After a short while, the windows with the plot of the sine functions will appear.
Desktop Access via Linux
Various RDP clients exist for Linux, and depending on your distribution, one is maybe already installed by default. Exemplarily, we use the client Remmina which comes natively on a lot of distributions, like Ubuntu. If you cannot start remmina directly, you could install it or use a different tool that supports RDP. CentOS users have to use the built in Remote Desktop Viewer Vinagre, for which the usage is quite self-explanatory.
The following instructions will show you how to start a RDP session with Remmina, but should be applicable to other clients as well:
Start the tool by opening a terminal and typing in remina or. Now you fill in the form as follows:
- Name: The name for the connection is for you to decide.
- Server: This is the login nodes server name.
- User name: The username that you use for every other university service as well.
- User password: The same goes for the password.
- Color Depth: If you get an error message when leavin this on standard, try True colour (32 bpp)
When you finished filling out the mask, click 'Save as Default' and then 'Save and Connect'. Now you will directed to the node. You may have to enter your credentials again, but after that you are good to go!
Desktop Access via Mac
For Mac, there is a simple solution to get a visual access to our X11 login note: Microsoft Remote Desktop 10.
(The HPC support team didn't test it though!)
Although this is a program for accessing Windows machines, it can be used to get access to linux machines as well.
Just download and install it from the app store, start the program and type in the host name (hpcl005.hpc.uni-oldenburg.de), your login name and the password.
For more information you can visit the programs support website
Important: Best Practices
If you are using an RDP connection to hpcl005, please be kind to other and aware of the following
- Save System Resources!
- hpcl005 is a login node with very few ressources. So please do not carry out heavy computations on this node! Instead run them remotely on a compute node using an interactive SLURM job (in particular, take note of the command srun.x11 that allows you to run graphical applications on a compute node). The login node hpcl005 is only intended for users who are dependent on a graphical interface and is designed for short testing sequences.
- Log out!
- When you have finished your work on hpcl005, please quit your programs within the terminal and finally log out of the graphic node. You can do this by clicking the 'power button' on the upper right corner and selecting your name which is displayed on the menu. Now you should see a Log Out option.
Using SSH Keys for login
SSH keys can make the login with SSH a bit more comfortable because they can remove the need to enter your password. The general idea is that a pair of SSH keys, one public and one private, can be used for authentification. The keys can be protected by a password (and the general recommendation is to do so), but it is also important to note that the private key should never be given to anyone. This means among other things that the private key file generated in the process described below:
- should not be copied, e-mailed or transferred otherwise to anyone else
- should be kept only on your own computer(s) and not be copied to multi-user systems (e.g. like HPC centers)
Please read the security considerations below for more details.
The following instructions show you how to create and use SSH key with the HPC cluster:
Creating SSH Keys
Windows
Microsoft started to roll out its own ssh client. But since it is not available on every Windows installation (and/or has to be activated), we use the SSH standard tool PuTTY (if you want to use the built-in SSH, you can use the Linux instructions below).
First of all, you need to download PuTTY. Click here and download the newest .msi file fitting your system (if you are not using an ancient PC, and are using Microsoft Windows, you very likely have to choose the 64-bit x86 installer ). Then, you execute the .msi file and click through the installation. You will need administrator privileges at this point.
Afterward, start the program PuTTYgen by searching for it on the windows search bar. In PuTTYgen you can set the parameters for the generation of an SSH key, and it is advised to use a 255 bit long EdDSA key (Ed25519). Chosing the PuTTYgen default algorithm RSA can get you in trouble with more current servers as this algorithm is by now considered to be less safe. Next, click Generate and you will be asked to move around the mouse a bit to generate some randomness. This produces two keys:
- Private key: This key is only for you and your devices. You must not hand this out to anybody!
- Public key: This key can be transferred to any machine that you want to login to with SSH (see below).
Optionally, you can now modify the key comment (it is recommended to add a meaningful comment) and also type in a passphrase (password) into the corresponding box. The password will be requested every time you establish an SSH connection using your key. Note: In general, you should type in a strong passphrase for your SSH key. Then, save the two keys on your local machine via the save buttons. The default location for SSH keys is:
C:\Users\USERNAME\.ssh
The files should be named id_ed25519.pub and id_ed25519 (if you created EdDSA keys) for the public and private key, respectively. Before closing PuTTYgen, also copy the public key text in the upper box to the clipboard, for this first right-click->select all and then right-click->copy.
Linux / macOS
Fortunately, Linux and macOS have all the tools you need already included. To generate a key pair, just open a terminal and type in
$ ssh-keygen -t ed25519 -b 255 Generating public/private ed25519 key pair. Enter file in which to save the key (/home/username/.ssh/id_ed25519): Enter passphrase (empty for no passphrase): Enter same passphrase again:
and follow the resulting prompts as shown above. You have the possibility to change the file name (typing enter uses the shown default) for the keys or to password protect it. Note: In general, you should type in a strong passphrase for your SSH key. After you have typed enter three times (one for the file, two for the passphrase), you have created two SSH keys:
- Private key: This key is only for you and your devices. You must not hand this out to anybody!
- Public key: This key can be transferred to any machine that you want to login to with SSH (see below).
The keys can be found at this location $HOME/.ssh and the files are named id_ed25519.pub and id_ed25519 (if you created EdDSA keys) for the public and private key, respectively. Now, copy the content of the public key into the clipboard by opening the following file with your favorite text editor: ~/.ssh/id_ed25519.pub
Add Public Key on HPC Cluster (or other Linux Hosts)
To enable the authentication with the generated key pair, you need to add the public key (id_ed25519.pub) to the authorized hosts list of the target system, e.g. the HPC cluster. This can be done in different ways:
Using the clip-board
After logging in to the cluster (not yet using the key), change to the hidden SSH folder in your $HOME directory:
cd $HOME/.ssh
and open the file authorized_keys with your preferred text editor. Go to the last line and paste the public key information that you copied clipboard in the step before. Make sure each key is in a separate line and do not overwrite existing keys in the file. Save the updated file and you are done.
Using the public key file
Alternatively, you can also copy the public key file id_ed25519.pub to the cluster. On Windows, use MobaXterm or WinSCP for that (do not overwrite any existing keys), on Linux you can use the command
scp $HOME/.ssh/id_ed25519.pub abcd1234@carl.hpc.uni-oldenburg.de:.ssh/id_ed25519.pub.yourcomputername
to achieve this.
The next step depends on the format of your public key. If you used PuTTy to generate the key it will likely be in a format as seen by the output (truncated) from this command
abcd1234@carl$ cat id_ed25519.pub.yourcomputername ---- BEGIN SSH2 PUBLIC KEY ---- Comment: "eddsa-key-20230308" AAAAC3NzaC1l....
where the first line is a delimiter. Otherwise, you will probably see
abcd1234@carl$ cat id_ed25519.pub.yourcomputername ssh-ed25519 AAAAC3NzaC1l....
where the key is in a single line.
If you have the first format, you can add the key using
$ cd $HOME/.ssh $ ssh-keygen -i -f id_ed25519.pub.yourcomputername >> authorized_keys
or, if you have the second format, simply use this command
$ cd $HOME/.ssh $ cat id_ed25519.pub.yourcomputername >> authorized_keys
Please note the double > for appending to the file authorized_keys. The commands also assume that you copied the public key to $HOME/.ssh/id_ed25519.pub.yourcomputername.
Login Using SSH Keys
Once you have created the SSH keys and added the public key to the authorized_hosts file on the cluster, you are ready to use the keys for logging in to the cluster.
Windows
Here, you can choose between the SSH clients as explained above: MobaXterm and PuTTY. We will shortly discuss how to setup the usage of SSH key in both of them:
- MobaXterm: Assuming, that you already configured a session (if not, see above), right-click on the corresponding session profile and select Edit session. At the rider Advanced SSH settings, tick the box Use private key and browse to the private SSH key that you saved earlier on. You can start the session now to test if the login with the key is working.
- PuTTY: Start PuTTY and load one of the saved sessions if you already stored a configuration (just loading, not starting). If not, type in at Host Name: abcd1234@carl.hpc.uni-oldenburg (change abcd1234 to your user name).
- In the left column, change to SSH -> Auth and insert your private key (Private key file for authentication). Change back to Session in the left column and save this session as a new file or overwrite an existing one. Start the session to test if the login with the key works.
Linux
In Linux, you just use ssh as always
ssh -X abcd1234@carl.hpc.uni-oldenburg.de
If for some reason, this does not use the key (e.g. because the key has non-standard name), you can try
ssh -X -i $HOME/.ssh/id_ed25519 abcd1234@carl.hpc.uni-oldenburg.de
to tell ssh which private key to use.
Using the SSH Agent
If you have created an SSH key with a passphrase (as is recommended) you need to enter the passphrase when you login:
[local]$ ssh abcd1234@carl.hpc.uni-oldenburg.de Enter passphrase for key '/home/abcd1234/.ssh/id_ed25519': Last login: Thu Jun 4 10:34:46 2020 from 10.0.40.110 [carl]$
The difference between the passphrase for the key and the normal password is that the password is sent to the remote server while the passphrase is entered only locally. The local passphrase is therefore considered to be more secure.
If you need to login multiple times to the remote server you can use the SSH agent to temporarily store the (unencrypted) private key. The command to start the agent and store a key are:
[local]$ eval $(ssh-agent -s) Agent pid 97 [local]$ ssh-add $HOME/.ssh/id_ed25519 Enter passphrase for /home/abcd1234/.ssh/id_ed25519: Identity added: /home/abcd1234/.ssh/id_ed25519 (/home/abcd1234/.ssh/id_ed25519)
Now you can login to the remote server
[local]$ ssh carl.hpc.uni-oldenburg.de Last login: Thu Jun 4 17:42:15 2020 from 10.0.40.110 [carl]$
without entering the passphrase again. To remove the key you can use
[local]$ ssh-add -d
or kill the agent process using the pid printed above.
You can also use
$ ssh -A ...
to enable agent-forwarding which allows you to use the private key also on the remote server, e.g. to login to a third system. Agent-forwarding removes the need to copy private keys to remote servers but it should only be used if it is really needed.
Security Consideration
The SSH protocol has designed to allow a secure access to remote servers. However, there is never absolute security and even HPC centers can be the target of hackers. To minimize the risk,
- do not give passwords or private keys to anyone (HPC support will never ask for your password)
- consider using SSH keys as this reduces the risk for man-in-the-middle attacks
- when using SSH keys kept your private keys secure and use a strong passphrase
- do not copy private keys to multi-user systems such as HPC clusters
- keep track of your authorized keys and use a pair of keys only for one system
- if you think any of your accounts were compromised make sure to change passwords and SSH keys
- if in doubt or if you detect unusual activities on your account contact Scientific Computing
VPN: Internet / From Home
If you want to work from home or from any other place outside of the campus network, you have to establish a VPN tunnel to the university's intranet. After that, you can login to CARL or EDDY via ssh as described above. See the following instructions on how to setup the VPN tunnel (please note, that IT services have recently changed to the new provider/protocol GlobalProtect for VPN. The old Cisco VPN will be available for some time but eventually removed, of course not before an announcement):
Windows
Download the VPN-Client from this web site and install it following the instructions of the IT Services.
After installing the software, you only will be prompted for your university user name and password once.
Linux
Download and Installation
At first, you will need the installation file from here.
- For Debian and derivates (e.g. Ubuntu) you will need the .deb file.
- For Red Hat, Centos, Fedora, Mandriva, OpenSUSE etc. you will need the .rpm file.
- If you want/need, you can get the source files with the .tgz file should you need to compile the software by yourself.
Now, you need to install the downloaded packet:
For Red Hat, Centos, Fedora, Mandriva, OpenSUSE etc.:
sudo rpm –ivh /path/to/GlobalProtect_rpm_x86_...rpm
For Debian and derivates (e.g. Ubuntu):
sudo dpkg –i /path/to/GlobalProtect_deb_x86_...deb
Alternatively, you can change to the same directory as the downloaded file and make sure that you type in the missing version. e.g.:
cd ~/Downloads sudo rpm –ivh ./GlobalProtect_rpm_x86_64-5.0.1.0-10.rpm
After the installation, the executable globalprotect is callable from the command line.
Configuration
With globalprotect connect to the portal v-uol.uol.de <br\> Type in your credentials when asked.
$ globalprotect connect --portal v.uol.de username: <Nutzerkontoname> password: <Nutzerkontopasswort> Connecting... Connected
Status and Connection Details
You can always check whether your connection is set up or not:
$ globalprotect show --status
Should you want to know more details about the current connection, you can type in:
$ globalprotect show --details
Finally, if you need to disconnect your VPN connection, you can use
$ globalprotect disconnect
Special Case: Linux Mint
If you are using Linux Mint 19, you will additionally need to patch Global Protect after the installation. <br\> This is what you have to do:
$ wget https://uol.de/fu/itdienste/download/update_gp_client.sh $ sudo sh update_gp_client.sh
Fall back method
If, after trying the above, you cannot setup you VPN using the Global Protect, you can try to install openconnect with
sudo apt-get install network-manager-openconnect-gnome
After that, you can set up a connection with the terminal command:
sudo openconnect --protocol=gp v.uol.de
As long as the terminal stays open, every packet will be sent through the universitys network first. To terminate the connection, just close the Terminal or type in STRG + c